
I’d like to begin with, and occasionally interject, along this sparse journey of the history of DRM, recollections on the hoops that Users, from mostly long dead threads, went through coping with ever changing technology, along with nostalgia for the good ol’ days of computing, while not forgoing the odd choices software developers made on this winding road to a still imperfect DRM system.
To begin, Chris, on the Hackaday Forum recollects: “I remember Battle Chess in the ’80’s, [the] DRM was archaic, but effective. It asked for a word [from the provided booklet], giving you the page and word number to look [it up] in. Luckily, the manual was only about 10 pages.”
What the Heck is DRM?
Somehow, I’ve almost forgot to define DRM. To do so, I’,m borrowing a quote from a 2006 issue of Insecure Magazine, in the article Digital Rights Management the author, Phillip J. Windley, hits the nail on the head: “Digital rights management (DRM) […] provides mechanisms for controlling the particular uses to which a digital resource can be put. This is a tough problem, [...] good solutions are sufficiently draconian.” Sure, DRM had innocent roots, in the heyday of software on floppy, developers wanted paid for their brow-sweat, but too often those who honestly bought software couldn’t back it up, and sometimes, due to dubious or less than ethical methods of DRM, couldn’t even use the software. Leaving us with a technology that, at times, may be defined as overkill.

Back in 1990, a gaming journalist wrote this in Compute, [Strategic Simulators INC] perfected its AD & D (Advanced Dungeons & Dragons) game system with the release of Champions Of Krynn. The article goes on to discuss graphics, strategy and gameplay, Yet, archaic forms of DRM are our interest. The writer went on to say “SSI packages a rule book and an adventurer's journal. Both booklets are organized well and also act as copy protection. Or as the data card reads:
“Answer the verification question by finding the indicated a word in either the Adventurer’s Journal or the rule book (the 16 page booklet with the same picture as on the cover of the game box). Type the indicated word and press ENTER/RETURN.”
The Early Days
Hackable and archaic DRM indeed. However, DRM didn’t begin with video games of the 1990’s. To trace the roots of Digital Rights Management, not to go too far off into the weeds, we must travel back to the mid 1970’s. At the time, a small startup, called Microsoft, created an operating environment (OS) that they dubbed Altair BASIC, it ran on the first mass distributed personal computer, the Altair 8800, an oversized glorified Calculator.
Those were the days before floppy disks, or even tapes. Altair BASIC ran off of a ribbon of paper. One day and ingenious fella came along with a high speed hole punch riveted fifty copies of the OS. He later distributed the pirated software at the Homebrew Computer Club. Microsoft, was not too happy about nogoodniks plagiarizing their brow-sweat, the software. Microsoft, as well as other up-and-coming tech commodities decided it was high time to stamp out freely distributed software.
In the early 1980’s, although this technology goes back to 1951, some software was released on tape cassette. Tape cassette programs, believe it or not, had DRM, it was simply a write protection tab in the bottom of the cartridge, the computer, as did tape decks, had a rudimentary mechanism that spotted the write protection tabs, if the holes existed, the tape couldn’t be copied, but this was easily defeated by sticky tape or a gob of glue.
I, the editor, had a copy of Buck Rogers by ColecoVision for the Adam System, The PC had 2 tape decks, I simply covered the write protection tabs on the bottom of the cartridge, copied it and distributed it to anyone who wanted the game. When I got bored of the forward-scrolling rail shooter (as the gaemplay is described), I used the tapes to record music. DRM aside, the most interesting things about the cassettes were that if you put them in an ordinary tape deck, they spat-out 8-bit avant-garde music, a surreal experience especially if thrown in a Teddy Ruxbin.
On-Disk DRM
By the mid 80’s, cassette based software gave way to “the floppy revolution.” At that time, a not hack proof, but somewhat effective copy protection system came about, a technology dubbed On-disk copy protection, During the manufacturing process, sneaky, or perhaps companies looking after their own interest, embedded DRM technologies into their floppies. For instance, intentionally bad sectors, odd address marks, different track layouts, file encryption and the notorious hidden 41st track became part of Apple and DOS software. But, Apple was particularly aggressive with on-disk DRM shenanigans.
Dirkt, on the Hacker News Forum recollects that ‘My favorite [form of DRM] is the spiral tracks on the Apple II, which were possible because all phases of the stepper motor were directly accessible on the controller, so you could move the stepper motor in quarter tracks. Impossible to copy unless you reproduce the head movements at the right time.”
It was a tricky DRM scheme, the Apple II would step the head in increments as the disk spun. Normal floppy copy software couldn’t deal with this. To further complicate Apple’s DRM, the Apple II disk controller was temperature unstable, software would only load when the computer was cool, room temperature.
Djimps, on the Hacker News Forum, gave this workaround for the pesky Apple On-Disk DRM. To duplicate the disks we ran our disk drives with the cases off [because of this] we could adjust the speed screw to match track lengths. We had software that would visually feedback the track length so you could get it spot on.”
It wasn’t just Apple using this technology, DOS experimented with similar schemes. And although On-Disk Protection made it hard for the novice to copy software, Hackers founds ways:
Jedberg, on the Hacker News Forum said “my favorite copy protection was on some games I had where [the software company] would cut the hole in the disk just slightly bigger, and then take advantage of the fact that in DOS you could talk directly to the hardware to convince the read-head to go just a little too far. Then it could read the magic 41st track to load the game, but no disk copy program could copy it.”

I would like to include an honorable mention here, although it’s a rare and collectible Nintendo proprietary DRM system only distributed in Japan, for the most interest On-Disk DRM, some Nintendo cartridges used the Nintendo logo and as form of copy rights management. Sure, the Fujifilm disk shown above had a hole that prevented making bootleg copies, but have a look at this:

FujiFilm’s hole-in-a-disk was cromulent, but this is Japanese ingenuity of the 80’s.
When it comes to ordinary forms of On-Disk DRM, popular software like VisiCalc and Lotus 1-2-3, to everyone's chagrin, had Apple’s On-Disk DRM. Why such chagrin? Because of this over engineered mess, everyday Users couldn’t backup the software they paid for with their hard earned money. And, if you had to deal with floppies as a form of data storage, you know that they are temperamental, fickle even, temperature sensitive, susceptible to mishandling and randomly became corrupted, all of this was a headache and sometimes called for a failed term paper (it happened to me once), but throwing less than perfect DRM into the mix and floppies too often became nothing more than a coaster with your data entombed within. This lead to the next generation of DRM, Off-disk copy protection.
Off-Disk Copy Protection
During the mid-to-late 80s, this became the most common method of copy protection and it was often promoted as a selling point on game boxes and other software. This method involved the game, or software, instructing the User to look into something in the manual, sometimes regarding a feature of the game or teaching you something about gameplay. At times, not always, but sometimes it had a dual purpose, Gamers learned game lore or founds easter-eggs while they proved themselves to be the rightful owner of the software.
Kelly Gray, on the Hackaday Forum recollects that “the best copy protection I ever saw was from Borland [a company that produced IDEs for C++ among other things]. You really needed to have the reference manuals for their compiler software, and they sold the software, complete with printed and bound manuals, for less than the cost of photocopying the manual.”
Games like X-Com: UFO Defense asked Users to type in a code that appeared on a given page. “Other games took it a step further and asked for a specific word from a given line in a given paragraph on a given page,” recollects a gaming journalist at Vintage Computing and Gaming.
AD & D (Advanced Dungeons & Dragons), had Users find something in the manual, easy enough for most Users, and hackable for those who wanted to share the software as if it were sold under a GNU license, but the era’s eggheads were no dummies, and so they introduced the next generation of Off-Disk DRM, The Code Wheel.
Code Wheels
And then the code wheel came along, another gamified form of DRM. The most famous disk of DRM is the wheel that came with The Secret of Monkey Island, released by LucasFilms Games in 1990. They called their off-disk DRM Dial-A-Pirate. It was literally a paper disk with pictures of pirates.
To prove yourself as the rightful owner of the software, you had to identify a pirate using random information in the game by spinning the wheel to reveal certain information about a pirate.
This was also easily hackable for those who wanted to share the software, just take the wheel apart, photocopy the pieces, cut holes in the right spots, glue it back together, share the copied floppy and disk.

Tinkeringdadblog, on the Hackady Forum recollects that “[there was a] a baseball game I had as a kid, it came with a circular spinning disk, you had to spin to the right combos and then enter the value at the center to get into the game. We just took it apart and copied it.”
Because an old lady in her crafting circle could foil the system, tech companies abandoned the concept for Code Sheets.
Code Sheets
Another method of Off-Disk DRM was The Code Sheet, and while this method was less complex, in regards to mechanical engineering (it had no moving parts), than code wheels, they were printed in such a way that prevented photocopying. For instance, The Humans, produced in 1992 by Imagitec Design, came with this Code Sheet:
Quinn Dunki, on the Hackaday Forum recollects that “a related technique was to make the code sheets very low contrast to foil photocopiers. SimCity, for example, had a code sheet printed in brown-on-beige.”
And then there were games like *Jet Set Willy* which didn't use codes but colors, see the below image for a description, from the manual on using this convoluted and possibly headache inducing form of DRM.

Andy Pugh on the Hackaday Forum recalls that “the idea was that, as color photocopying didn’t really exist then, a photocopy of the instructions wouldn’t work. But they reckoned without the ingenuity of the copy makers, who simply wrote down r, g, etc for the colors on a matching grid and photocopied that.”
Games like SimCity had sheets with dark-colored codes, which you could see in the right light, but a copy machine couldn’t reproduce them. Then there were games like Dragons Lair, it had a code sheet nobody could see (The eggheads at Readysoft printed it in monochromatic gray). Along the same lines, other game makers concocted puzzle based DRM, but it was all a failure and hackers found loopholes. And so, Lenslok technology came along.
The Flop that was the Decipher Code: Lenslok
It was 1985 and 11 games came with a rectangular foldable piece of plastic. The technology was called Lenslok. This 1950’s comic book backpages spy gadget (it was a plastic lens that allowed the User to read hidden text) like device came with transparent prisms in the monocle-like lens that reflected light to decipher encrypted text on a television.
To defeat the DRM, you had to type in the deciphered code into the game’s start screen. Essentially, it was mechanical DRM. It was so bad, a gaming journalist at crappygames.com had this to say:
“It was a flop, and in the end, all of the games that supported Lenslok were eventually patched to remove Lenslok protection, with some of them replacing it with manual-based copy protection.”

The Journalist even went on to list 8 reasons why Lenslok sucked, they can be found here
The Short Lived Era of the Dongle
Dongles appeared in the early 80’s and were used both for games and commercial software like TypeCraft, an online application consisting of a natural language database and a linguistic editor for interlinear glossing (1982). It plugged into a computer's communication port, the computer refused to allow the software to run unless it was detected. Mostly, the dongle was used for higher end software but a few games have used it over the years, notably, Robocop 3 by Digital Image Design in 1991.
Dave on the Hackaday forum recollects “Robocop III [came with a] dongle which needed to go into the second joystick port. It pushed the price to an astronomical £35 for a computer game. [the dongle DRM] was cracked mere hours after release on the BBS’s.”

With the end of the 80’s, floppies, cartridges and software on cassette gave way to CD-ROM.
CD and CD-ROM DRM
Systems like SafeDisc, SecuROM and StarForce attempted to prevent both piracy and backing up the software and music that came on those flimsy and easily scuffed media vaults we call CD. Why didn’t Mini Disk take off? I guess Sony dropped the ball on that.
SafeDisc, SecuROM and StarForce applied digital signatures or electronic fingerprints to the disk during mastering. This assigns a unique number to the disk. It’s said that SafeDisc used a more simplistic method of DRM, it wasn’t “terribly intrusive or tough to bypass,” as Clint from the YouTube channel LGR has said. Yet, SecuROM was a tough nut to crack. However, StarForce’s DRM is the most infamous. There were claims that their DRM was nothing less than malware - it degraded optical drive performance with continued use. It did so by installing a rootkit.
FADE is another DRM technology that acts like malware. It was used in FPS games like Operation Flashpoint and Arma II. This system gradually degraded pirated copies of games.
Dance Mentor on the Dance Forum laments that “[Even]the new Beastie Boys new CD (in some countries) silently installs Digital Rights Management software on your computer without your knowledge.”

The Beastie Boys' CD, To the Five Boroughs (Capitol Records, 2004), is covertly installing an executable file on your Windows or Mac box, Linux is spared from this travesty. On Windows, when a CD is loaded, a text file called autorun.inf is read, and any instructions within it are executed. In this case, the machine is instructed to install some manner of DRM driver that prevents copying. This is the malicious side of DRM, there’s speculation the the file may not allow User to copy or share other files they own.
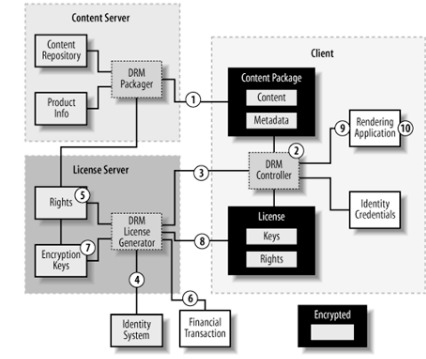
SAAS
When Software As A Service came along, of course, the folks behind these streaming video games online XML editors and etc needed to protect their creations from nogoodniks. To do so, a client verification server runs silently in the background. Online DRM often works like this, you mostly likely have limited installs of a specific piece of software, once installed the software creates a .config file that states that you have installed this on 1 of x machines. The whole online activation process is accomplished through a serial number. This is true for Steam, Games for Windows Live, Origin and Uplay. Although, among Gamers, Steam is considered a more seamless DRM/gameplay experience, all the services, Steam included, have DRM issues that negatively effect the average User.
Clint from the YouTube channel LGR noted that [Unisoft’s] Anno 2070 [a city-building and economic simulation game on Steam] is a recent example of [SAAS DRM going horribly wrong] even if you change your graphics card, [the game] treats your PC like an entire new computer, using up one of your 3 installations”
Worst of all, all SAAS DRM systems require a constant internet-connection. “This is DRM that is always online, always connected, always watching, always planning, better have a reliable broadband connection and an outstanding router," states Clint. And, if you can’t connect to the service’s server, which may be located in Timbuktu, to save money, you can’t play the game you paid hard earned cash for.
The Difference Between DRM and IRM
IRM is used to protect the highly sensitive information that may be contained in a document. A hospital may, for example, apply IRM to patient records in order to maintain compliance with HIPAA-HITECH, whereas games use DRM, in all the technologies are similar and follow parallel archs, up until a point DRM is still grappling with hacky technologies and IRM has mastered data encryption and two-point-verification.
